I’ve recently been asked how to configure the Citrix NetScaler administration GUI console with a secure certificate so that the login credentials would not be passed in clear text and while I’ve done this numerous times without giving the process much thought, I never wrote a blog post about it. Doing a quick search on the internet did not appear to return a Citrix KB that clearly showed up to do it so this post serves to demonstrate the process.
Before I begin, the closest Citrix KB that resembles this task is the following:
How to Enable Secure Access to NetScaler GUI Using the SNIP Address of the Appliance
http://support.citrix.com/article/ctx111531
The article in the link above demonstrates how to configure a SNIP (Subnet IP) that allows NetScaler administration GUI console access and while there are many benefits in doing so, if configuring an additional SNIP for GUI access is not desired, we can achieve the same results with the NSIP as well.
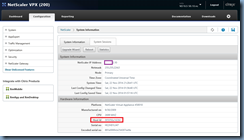
First off, the NetScaler NSIP is actually configured with the default ns-server-certificate certificate by default and is indeed listening on port 443 (https) as shown here:
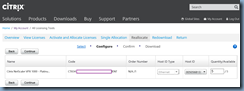
NetScaler –> Traffic Management –> SSL –> SSL Certificates
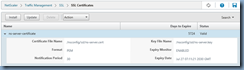
The problem here is that the key size is only 512-bit and browsers today would refuse to connect to a website that uses a certificate that is 1024-bit or less:
This is why you receive the following webpage if you try to use https://<netScalerIPorName> to access the GUI administration console:
There is a problem with this website’s security certificate.
The security certificate presented by this website is not secure.
Security certificate problems may indicate an attempt to fool you or intercept any data you send to the server.
We recommend that you close this webpage and do not continue to this website.
Click here to close this webpage.
More information
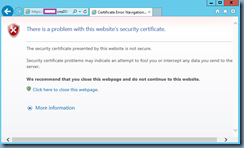
If the default certificate was at least 1024-bit then you would have gotten a choice to proceed but because the bit level does not meet the minimum requirements of the browser, you are left with only the option to close the webpage and terminate the session.
Step #1 – Request and Install a valid SSL Certificate
A valid certificate must be installed prior to enabling SSL access to the NSIP GUI and since I’ve written a blog post in the past about this, I’ll simply refer to it rather than outlining the steps again:
Generating CSR and installing certificate on NetScaler VPX 1000
http://terenceluk.blogspot.com/2012/10/generating-csr-and-installing.html
Step #2 – Assigning a SSL Certificate to the NSIP IP
The KB article I listed above demonstrates the process of configuring the SNIP via CLI but here I will demonstrate how to configure it via the GUI. Begin by logging into the NetScaler’s GUI console and navigate to:
NetScaler –> Traffic Management –> Load Balancing – Services –> Internal Services
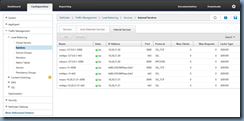
The IP address that represents the NSIP of the NetScaler are as follows:
- IPv4 – nshttps-127.0.0.1-443
- IPv6 – nshttps::1|-443
Proceed by opening the properties of nshttps-127.0.0.1-443 to display the configuration settings:
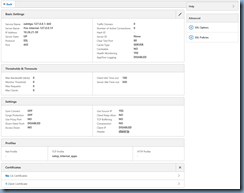
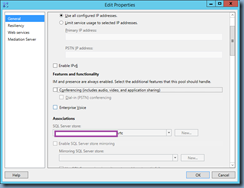
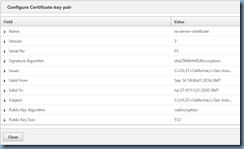
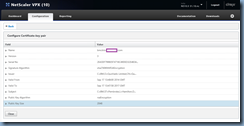
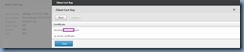
Navigate to the bottom of the list and click on Client Certificate to bring up the Client Cert Key window:
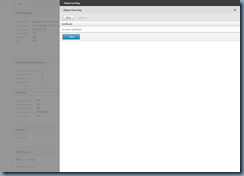
Note how the default 512-bit ns-server-certificate is binded as a Certificate already which is why the NetScaler administration GUI console listens on port 443 (https) but is rejected by web browsers. A proper certificate should be 1024-bit or higher and the one I’ve installed for this example is 2048-bit as shown here:
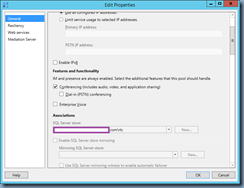
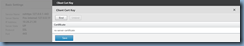
Proceed by clicking on the Bind button to list the certificates available:
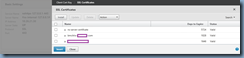
Select the certificate that you’ve imported in Step #1 and click on the Insert button:
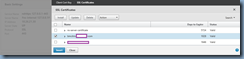
Proceed with unbinding the default certificate (if you forget, the NetScaler will unbind it for you) and click on the Save button:
You should now be brought back to the previous page and with the certificate binded, proceed by clicking on the Done button:
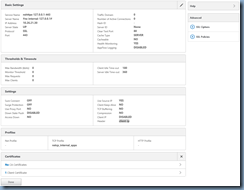
With the new 1024-bit or higher certificate binded, your NetScaler GUI administrator console should now load properly via https:


Repeat Step #2 for the IPv6 NSIP nshttps::1|-443.
Step #3 (Optional) – Forcing https Access to NetScaler
Depending on the organization’s security requirements, policy may dictate that all traffic to the NetScaler’s GUI administration console must be encrypted so if this is the case, it is possible to disable http access to the NSIP. Note that I’ve been asked many times whether there is a way to simply do a redirect and the answer is “I don’t know” as I have yet to come across information on how or whether this can be done so feel free to let me know if you do.
Begin by navigating to:
NetScaler –> System –> Network –> IPs –> IPV4s
… then select your NetScaler IP:
Open the properties page of the NSIP:
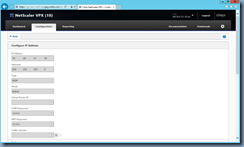
Navigate to the bottom of the configuration page and locate the Secure Access only checkbox:
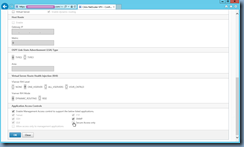
Checking this checkbox will disable http access:
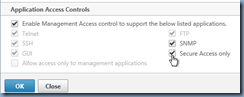
Once this has enabled, you will no longer be able to access the GUI via http:
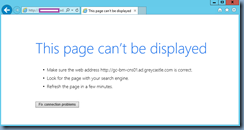
Not surprisingly, I’ve been called several times about not being able to access the GUI administrator console after enabling this because of reasons such as there was something wrong with the certificate used for https traffic or the administrator forgot to bind the certificate. While you cannot access the GUI anymore, you can still SSH over to the NetScaler to disable the Secure Access only option via command line. The command to disable forced https access is as follows:
set ns ip <NSIP> -gui enabled
Using the IP addresses in the screenshot above as an example, the command would look as such:
set ns ip 10.26.21.30 -gui enabled
Conversely, if you wanted to enable the Secure Access only option via CLI, the command would like as such:
set ns ip 10.26.21.30 -gui secureonly
-------------------------------------------------------------------------------------------------------------------------------------------------
Hope this helps anyone out there looking for instructions on how to secure NSIP GUI access.