One of the most common questions I’ve been asked by clients is whether there is a way to audit administrators granting Full Access permissions to mailboxes in Exchange and the answer to that is yes because every action made within the Exchange Admin Center or Exchange Management Console can be logged by a feature named Administrator Audit Logging which basically logs every mirror Exchange cmdlet executed that isn’t a Get-.
Enable Administrator Audit Logging
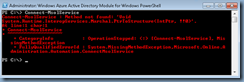
The first step in the process of providing auditing logs is to execute the following cmdlet to ensure that logging is turned on:
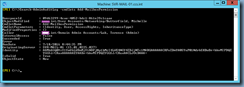
Get-AdminAuditLogConfig | FL
Notice that the AdminAuditLogEnabled is set to True while the LogLevel is set to Verbose. If the configuration is set to any other setting, execute the following to change it:
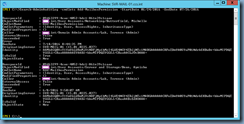
Set-AdminAuditLogConfig -AdminAuditLogEnabled $true
Set-AdminAuditLogConfig -LogLevel Verbose
More information about the Set-AdminAuditLogConfig can found at the following TechNet article: https://technet.microsoft.com/en-us/library/dd298169(v=exchg.160).aspx
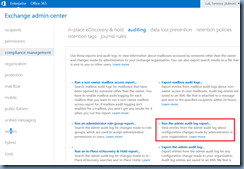
Audit Option #1 - Review Admin Audit Log Report
Once administrator audit logging is enabled, we can review the Compliance Management > auditing > Admin Audit Log Report from within the Exchange Admin Center:
… configure a Start date and End date to narrow the return results:
Then sort the CMDLET column by alphabetical order and look for the cmdlet:
Add-MailboxPermission
or
Remove-MailboxPermission
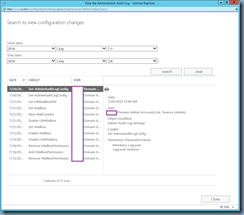
… to review when and which administrator made the changes:
Audit Option #2 – Using PowerShell to search admin audit log
Another method for reviewing the admin audit log is to use PowerShell to search it and the cmdlet that allows us to accomplish this is Search-AdminAuditLog (TechNet: https://technet.microsoft.com/en-us/library/ff459250(v=exchg.160).aspx). The following cmdlets searches for either Add or Remove of mailbox permissions:
Search-AdminAuditLog -cmdlets Add-MailboxPermission
Search-AdminAuditLog -cmdlets Remove-MailboxPermission
Note that executing Search-AdminAuditLog without any parameters will only parse through 1,000 entries which may not cover a wide range of days so to ensure that specific dates are covered, include the StartDate and EndDate switches as such:
Search-AdminAuditLog -cmdlets Add-MailboxPermission -StartDate 01/24/2016 –EndDate 07/26/2016
Audit Option #3 - Review Admin Audit Log Report
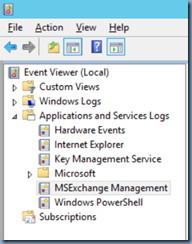
The last option available is to review the event logs Applications and Services Logs > MSExchange Management logs in the Event Viewer:
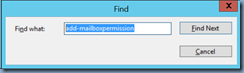
Simply right click on MSExchange Management select Find…:
Then search for Add-MailboxPermission:
---------------------------------------------------------------------------------------------------------------------------------------------------------------
Hope this helps anyone out there looking for a way to audit actions performed within Exchange.





















![clip_image002[6] clip_image002[6]](https://lh3.googleusercontent.com/-ulAEq88C_78/V30Bo5e3r0I/AAAAAAAB9PQ/Kq3_0HCiggc/clip_image002%25255B6%25255D_thumb.jpg?imgmax=800)